Want to know how hackers find your wordpress username? Details Inside

Technique 1: Using/?author=1 Query Parameter
At some point, I had quite recently set up another blog and thought I’d covered up my administrator zones really well. Incredibly, my security modules began sending me lockout takes note. This implies that in addition to the fact that hackers were ready to discover my login page, they had the option to figure my WordPress username too! I opened up my crude access signs in cPanel, and discovered this:
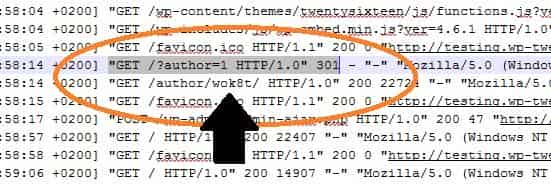
Evidently, programmers can discover your username in WordPress by affixing the inquiry/?author=1! You can find in the screen capture over, that my worker quickly returned the creator page – which obviously, uncovered the username. So disregard making your username hard to figure. It’s privilege out there in the open!
Here’s what it looks like. In the first place, type in your blog name and type/?author=1 after the URL like this:
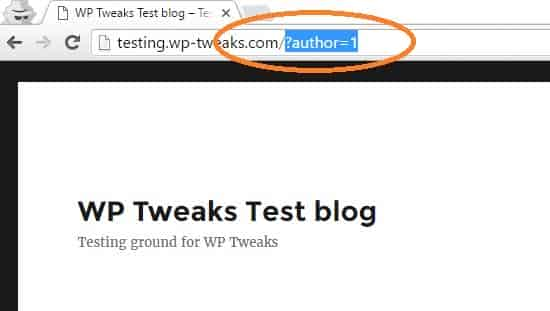
This will redirect to this page
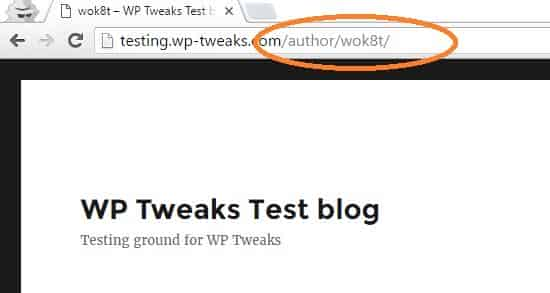
A few specialists guarantee that uncovering WordPress usernames isn’t a security hazard. As per them, making a solid secret key and utilizing two factor confirmation is the correct approach. However, I say there’s nothing incorrectly sequestered from everything however much data as could be expected from programmers. Possibly on the off chance that somebody is genuinely resolved to know my username, they can. However, that doesn’t mean I need to make it simple for them! I need expected assailants to attempt to break into my site. Ideally, this will prevent 90% of them.
In the event that programmers don’t have the foggiest idea about your username, they will not spam your site attempting to figure your secret word. This implies less burden on your worker. I’ve been cut down once before by programmers DDoS’ing my login page. I would prefer not to hazard that once more.
So how would we close this escape clause? There are two different ways to keep WordPress from uncovering your creator name through the boundary hack.
Fix 1: Modifying .htaccess
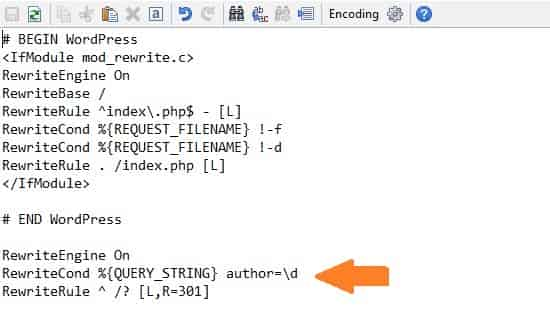
This is my favored procedure since it’s a lot quicker than the other option. By making a straightforward .htaccess rule, you can promptly impede all endeavors to get to your WordPress username through the ?creator boundary. In the event that you approach it, open the covered up “.htacces” record in the root registry of your WordPress establishment, and glue in the accompanying code toward the end:
RewriteEngine On RewriteCond %{REQUEST_URI} !^/wp-admin [NC] RewriteCond %{QUERY_STRING} author=\d RewriteRule ^ /? [L,R=301]
This is how the code will look like after you have made the changes to the .htaccess file
Fix 2: Adding a Code Snippet to WordPress
The subsequent strategy is to add a code scrap to WordPress that achieves something similar. In the event that you don’t have the foggiest idea how, read my previous bit by bit instructional exercise on the most proficient method to do this. Here is the code you need to glue into your custom module or functions.php:
function redirect_to_home_if_author_parameter() {
$is_author_set = get_query_var( 'author', '' );
if ( $is_author_set != '' && !is_admin()) {
wp_redirect( home_url(), 301 );
exit;
}
}
add_action( 'template_redirect', 'redirect_to_home_if_author_parameter' );
Like the .htaccess code, this does the very same thing. It verifies whether you’re not in the administrator region, and whether somebody is attempting to get to the creator name by means of the “?creator” boundary. Assuming this is the case, it diverts back to the landing page.
The thing that matters is that this executes at the WordPress level, and is consequently marginally more wasteful than the main strategy. Yet, on the off chance that you don’t approach .htaccess, it’s the solitary alternate way. Checking your entrance logs will uncover precisely the same thing paying little heed to which strategy you pick.
So while some may reject that noteworthy usernames is a security danger, my rule is that the harder you make it for somebody to nose about your site, the better. Also, in the event that you need to forestall animal power assaults, and to keep programmers from discovering your WordPress username, one of these two bits of code will get the job done!
In case you’re taking a gander at truly benefiting from WordPress, you ought to consider specific facilitating. Various organizations have various arrangements, and you can see the correlations of the WordPress facilitating costs at one look.
Fix 3: Use Cloudflare Page or Firewall Rules
A ton of sites use Cloudflare in any case, so this is a simple arrangement. Simply add another page rule or a firewall rule to prohibit the risky URL. You can either divert the page to the landing page, or square it out and out. The free form of Cloudflare accompanies 3 free page rules and 3 free firewall decides that you’re presumably not utilizing in any case. So we should use them!
Technique 2: Using WordPress JSON REST Endpoints
Visit the accompanying URL on your WordPress site:
https://[yoursite]/wp-json/wp/v2/clients/1
Supplant [yoursite] with your site name. You ought to get something like this:
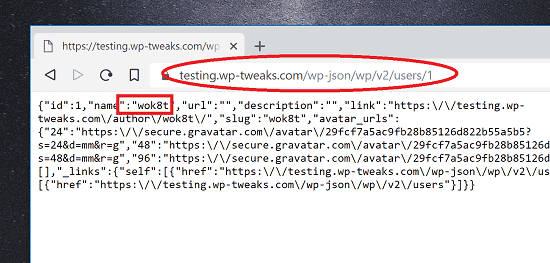
That is your WordPress username on display! This is on the grounds that WordPress uncovered certain REST APIs as a matter of course and this permits anybody to specify the clients by means of JSON.
Fix: Disable by means of Code
Luckily, we can simply impair these endpoints by means of this basic code scrap:
function disable_rest_endpoints ( $endpoints ) {
if ( isset( $endpoints['/wp/v2/users'] ) ) {
unset( $endpoints['/wp/v2/users'] );
}
if ( isset( $endpoints['/wp/v2/users/(?P<id>[\d]+)'] ) ) {
unset( $endpoints['/wp/v2/users/(?P<id>[\d]+)'] );
}
return $endpoints;
}
add_filter( 'rest_endpoints', 'disable_rest_endpoints');


