Globant, an IT giant, confirms a source code repository breach

Globant, an IT behemoth, has revealed a data breach after the notorious hacker gang Lapsus$ published tens of gigabytes of purportedly stolen data from the company.
Earlier this week, the hackers released over 70 Gb of source code purportedly belonging to Globant clients. The names of the folders indicate that part of the source code belongs to prominent corporations such as Apple and Facebook.
The gang has also published a list of usernames and passwords that they believe may be used to get access to other Globant development platforms.
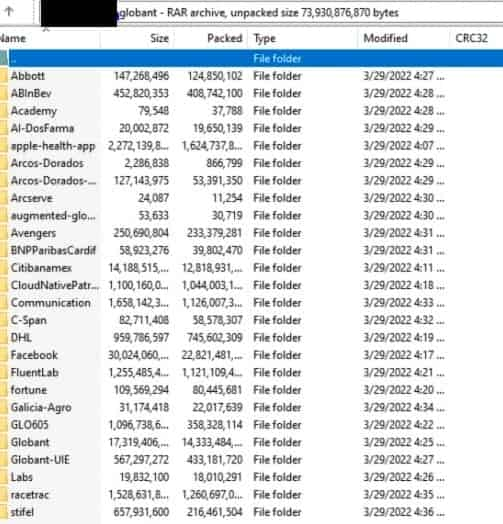
Globant said in a statement on Wednesday that it activated security mechanisms and initiated an investigation after discovering illegal access to a “small part” of its code repository.
“According to our current investigation, the information accessed was restricted to specific source code and project-related documentation for a very small number of clients.” “We have found no evidence that additional portions of our infrastructure systems or those of our clients were compromised,” Globant said.
The corporation employs over 23,000 people and has a presence in 18 countries. Google, Electronic Arts, and Rockwell Automation are among its clients.
Lapsus$ has claimed responsibility for assaults on a number of other big corporations, including Microsoft, Okta, Samsung, Vodafone, Ubisoft, and NVIDIA.
These organisations verified a data breach after the hackers made substantial amounts of information public, however the majority of the victims felt the hackers’ claims were overblown.
Lapsus$ declared its intention to pursue Globant less than a week after police in the United Kingdom announced the arrest of seven people ranging in age from 16 to 21 and thought to be associated to the organisation.
Lapsus$ is a financially driven group that steals data from significant corporations — often source code — and demands a ransom in order to prevent the stolen materials from being leaked.
To achieve their goals, fraudsters mostly rely on social engineering, compromising employee accounts, SIM swapping, and insiders, frequently naming and shaming victims on a Telegram channel.


