How hamas is using cute girls profile to catfish Israelis
APT-C-23, a Hamas-affiliated assault organisation, is accused of running a sophisticated catfishing operation aimed at high-ranking Israeli officials. Aside from extensive Facebook-focused social engineering, the gang has released new malware such as a phoney chat app (known as VolatileVenom), a downloader (known as Barbie Downloader), and a backdoor (known as Barbie Backdoor) (BarbWire Backdoor).
Individuals working in defence, law enforcement, emergency services, and other government-related groups are targeted by the campaign. Social engineering, a downloader, a backdoor, and a separate Android malware are all used in the attack. Espionage appears to be the goal. Cybereason’s Nocturnus researcher team found and studied the campaign.
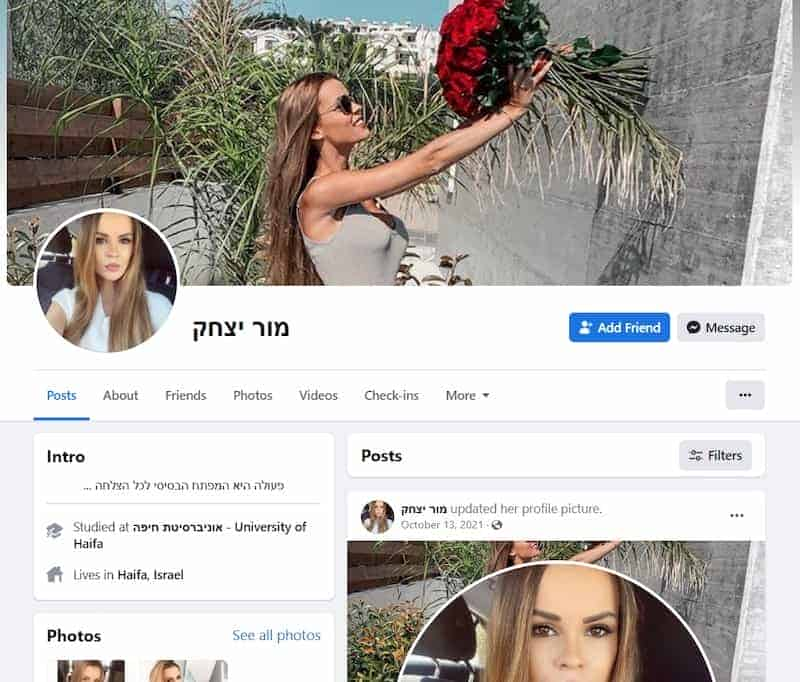
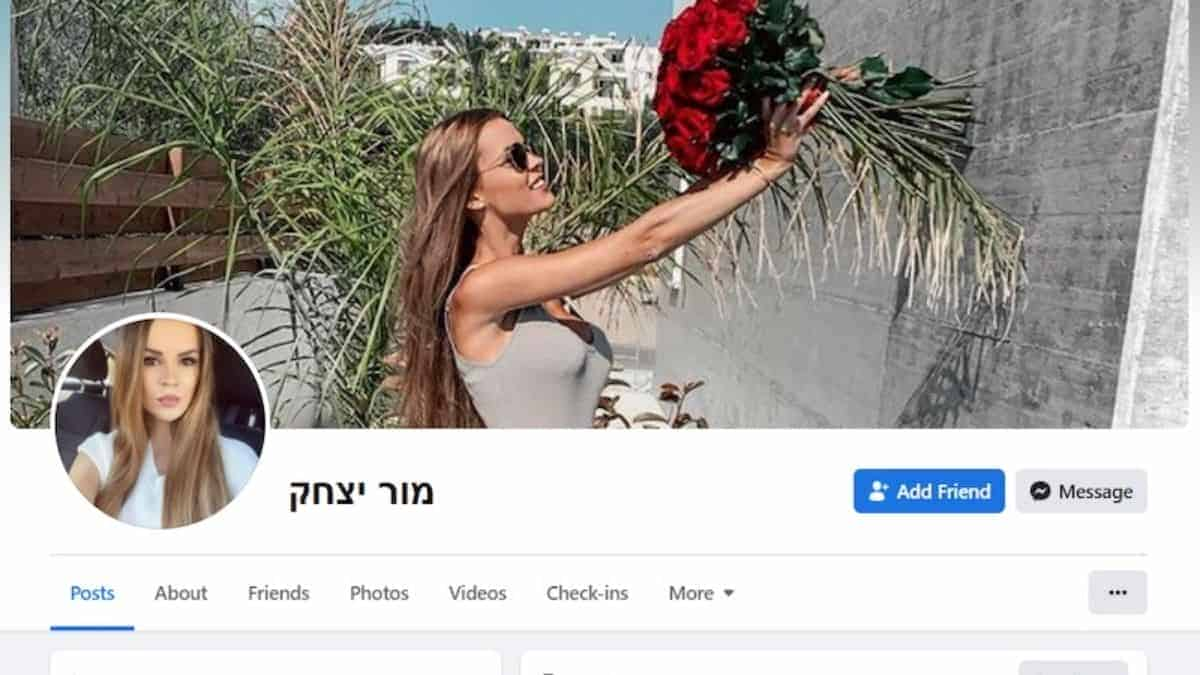
According to the experts, the attacks begin with a false (catfished) Facebook network of attractive females. The attackers joined relevant groups, posted in Hebrew to those groups, and friended friends of the targets, so the accounts are well-established and well-maintained. The goal is to establish a rapport with the officials and gradually entice them into a virtual sexual connection.
The catfish attacker proposes switching to WhatsApp after this link is established and Facebook chats are formed. This provides the attacker with the target’s phone number right away. The attacker advises they utilise a’safer’ and more ‘discrete’ method of communication as the chats become more personal and sexual. It is suggested that you use a specialised Android app.
The Hamas cyberwarfare section is thought to be divided into two sub-groups: APT-C-23 and Molerats. In most of North America and Europe, Hamas is considered a terrorist organisation. ‘Catfishing’ is the establishment of a false online identity based on part or all of a real one, with the goal of causing harm to people’s reputations. The goal in this scenario is to construct an extremely believable identity that may be used to lure victims in. Operation Bearded Barbie is the name of the current campaign.
The Android app is actually the virus VolatileVenom. The icon is concealed on pre-Android 10 devices; with Android 10, the virus utilises the Google Play installation icon. When the victim tries to sign into the app, however, an error message appears, stating that the app will be uninstalled. With a wide spectrum of espionage capabilities, VolatileVenom continues to function in the background.
Separately, the assailant offers to provide a private film to the victim. The video and the Barbie Downloader are packaged together in an a.rar file. “The film is supposed to distract the victim from the infection process that is taking place in the background,” the researchers explain. anti-analysis checks and system information collecting are part of the infection process.
If the host is deemed appropriate, the downloader connects to an embedded C2 server (otherwise it just terminates). The BarbWire Backdoor is delivered by the C2 server. The downloader contains a backup technique for finding a different C2. If the attackers need to modify the C2 from the one inserted, they can simply send an SMS message with the new destination. All incoming SMS messages are intercepted by the downloader. If one is provided by the attackers, it can simply extract the new C2 information and download the backdoor.
The Android app is actually the virus VolatileVenom. The icon is concealed on pre-Android 10 devices; with Android 10, the virus utilises the Google Play installation icon. When the victim tries to sign in to the app, however, an error message appears, stating that the app will be uninstalled. With a wide spectrum of espionage capabilities, VolatileVenom continues to function in the background.
Since September 2021, campaigns have been active. Despite the new malware and the more advanced social engineering element than normal, the Cybereason Nocturnus researchers believe the attackers are the Hamas-linked APT-C-23 gang ‘with moderate-high confidence.’ The campaign shows a “significant step-up in APT-C-23 capabilities,” according to the experts.
Other efforts against more frequent Palestinian and Arabic-speaking targets are still active, however, this one employs a different architecture than the recognised APT-C-23 infrastructure, as well as new malware developed particularly for Israeli targets. Some patients have been infected with both VolatileVenom and BarbWire Backdoor, according to the researchers. “The threat actors’ ‘tight grasp’ on their targets attests to how significant and sensitive this campaign was,” they write.


