New IoT RapperBot Malware target Linux Servers
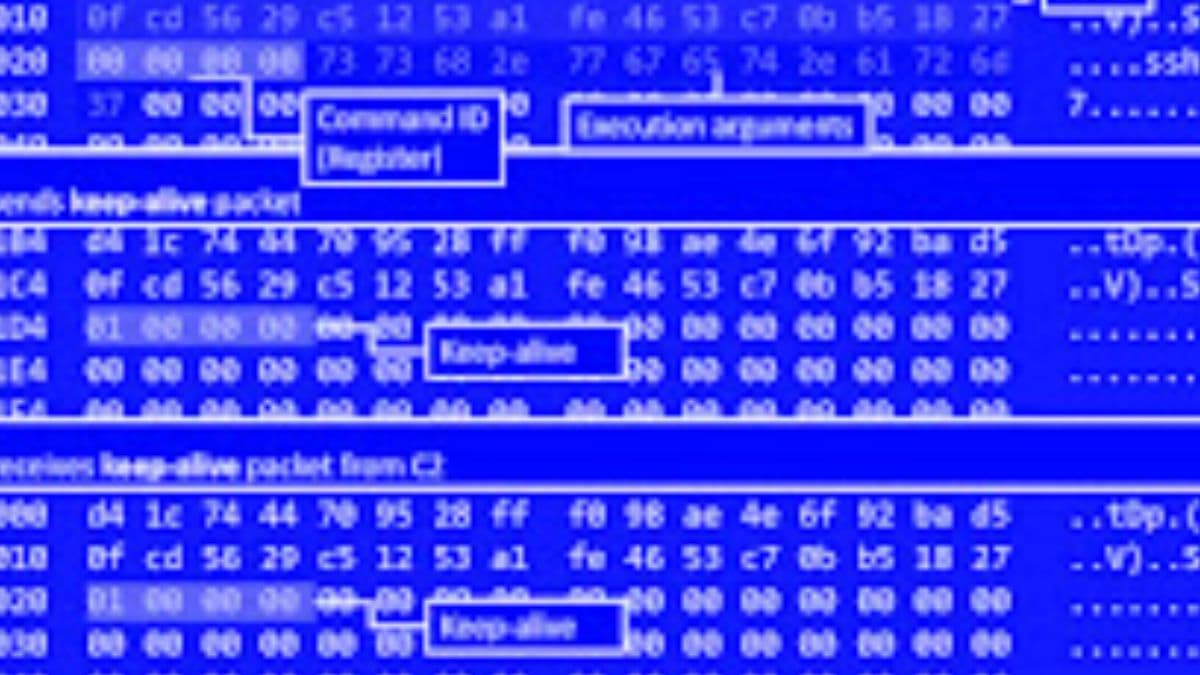 Image courtesy:cybersecuritynews.uk
Image courtesy:cybersecuritynews.uk
On Saturday, A new IoT botnet malware dubbed RapperBot has been observed rapidly evolving its capabilities since it was first found in mid-June 2022.
Fortinet FortiGuard Labs said that this family borrows heavily from the original Mirai source code, but what differentiates it from other IoT malware families is its built-in capability to brute force credentials and gain access to SSH servers instead of Telnet as implemented in Mirai.
According to Hacker News, the malware which got its name from an embedded URL to a YouTube rap music video in an earlier version is said to have gathered a growing collection of compromised SSH servers, with over 3,500 unique IP addresses used to scan and brute-force their way into the servers.
RapperBot’s current implementation also describes it from Mirai, letting it primarily function as an SSH brute-force tool with limited capabilities, carrying out distributed denial-of-service (DDoS) attacks.
The deviation from traditional Mirai behavior is further shown in its attempt to establish persistence on the compromised host, effectively allowing the hacker to maintain long-term access long after the malware has been removed or the device has been rebooted.
The attacks require brute-forcing potential targets using a list of credentials received from a remote server.


