How to Find Out If You Have Been Infected by RATs?

When you use the computer or mobile device for a variety of private or secret functions daily, it’s critical to safeguard it against viruses and spyware. A RAT, or Remote Access Trojan, is a sort of spyware that cybercriminals can use to get access to your computer or mobile device and seize command of it to steal your confidential info or eavesdrop on you. This is referred to as ratting. RATs are rapidly being used to get control of cameras to use the resulting movies or photographs for extortion or other illegal purposes.
RATs and Hackers

You might be acquainted with the beauty of remote access if you’ve ever had to contact tech assistance for a PC. Authorized computers and servers can regulate everything that occurs on your PC while remote access is permitted. They can access documents, download software, and even move the mouse around the screen in real time.
A remote access trojan (RAT) is a type of malware that looks very much like legitimate remote access tools. The primary difference is that RATs are deployed on a computer without the consent of the user. The majority of legitimate remote access tools are designed for tech help and file sharing, whereas RATs are designed to spy on, hijack, or damage systems.

RATs, like other viruses, prey on files that appear to be legal. A RAT can be sent to a document in an email or embedded in a major software package, such as a video game, by hackers. RATs can be found in advertisements and malicious websites. However modern browsers prohibit automated downloads from websites or alert you when a site is hazardous. It’s impossible to identify when you’ve downloaded a RAT, unlike some spyware and viruses. In general, a RAT won’t slow down your computer, and hackers won’t always delete your files or move your cursor around the screen to reveal themselves. Users can be infected by a RAT for years before detecting anything is wrong.
Being Infected by RATs – How?
The majority of computer viruses are created with a specific goal in mind. Keyloggers capture everything you type, ransomware prevents you from accessing your computer or files until you pay a charge, and adware displays questionable advertisements on your computer for money. RATs are frequently utilized in the same way as spyware is. A RAT can be used by a money-hungry (or creepy) hacker to acquire keystrokes and files from a compromised system. Bank information, passwords, personal images, and private chats might all be found in these keystrokes and files. Hackers can also employ RATs to covertly activate a computer’s webcam or microphone. The prospect of being watched by some unknown nerd is unsettling, but it’s nothing compared to what some attackers do with remote access tools (RATs).
Even though RATs offer hackers admin privileges to infected systems, they can change or download any file they want on the go. That means a hacker with a RAT can delete your hard drive, download unlawful content on the web through your computer, or infect your computer with other software. Hackers can even utilize your home network as a proxy server to break laws discreetly or remotely manipulate your computer to perform humiliating or criminal behaviors online in your identity.
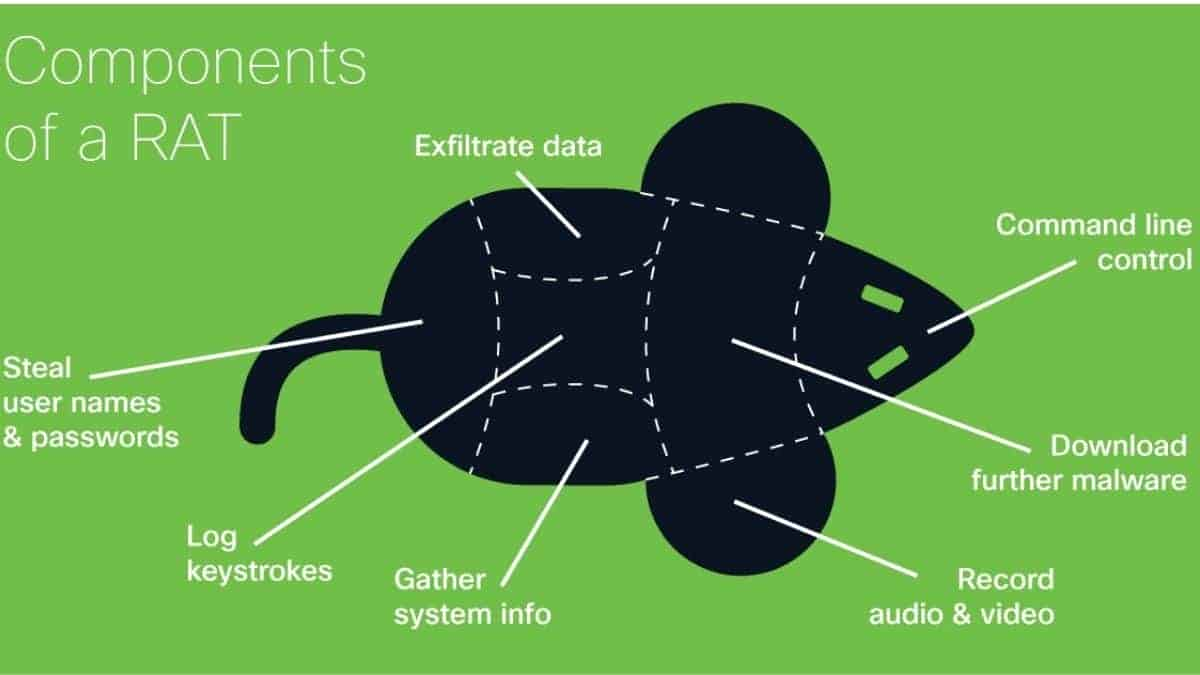
A RAT can also be used by a hacker to get control of a home network and establish a botnet. A botnet, in essence, allows a hacker to use your computer’s resources for nerdy and often illegal things like DDOS attacks, Bitcoin mining, file hosting, and torrenting. Hacker groups have used this tactic in the past for cybercrime and cyber warfare. A botnet made up of thousands of machines can generate a lot of Bitcoin or use DDOS assaults to bring down huge networks or perhaps an entire nation.

Get Rid of the RATs
If you prefer to prevent RATs, don’t download the data from untrustworthy sites. You shouldn’t click links or attachments from outsiders, and you shouldn’t download stuff or software from unusual websites unless they’re from a reliable source. Also, make sure your browser and operating system are up to date on security fixes.


