3 Web Domains have been Confiscated by the Department of Justice which were used for DDoS Operations and Trade Stolen Data

As per the news floating around the internet, it claims that the US Department of Justice (DoJ) claimed in a news release on Wednesday that it had seized three web domains used by malicious attackers to execute distributed denial-of-service (DDoS) operations and sell stolen personal data.
During the announcement, the FBI and the Department of Justice, according to US Attorney Matthew M Graves, were able to stop two distressingly widespread threats: websites that trafficked in stolen personal information and sites that attacked and disrupted legal internet enterprises. Cybercrime frequently crosses national lines, according to Graves. They will fight crimes like these that endanger privacy, security, and trade around the world by relying on strong working ties with our international law enforcement agencies.
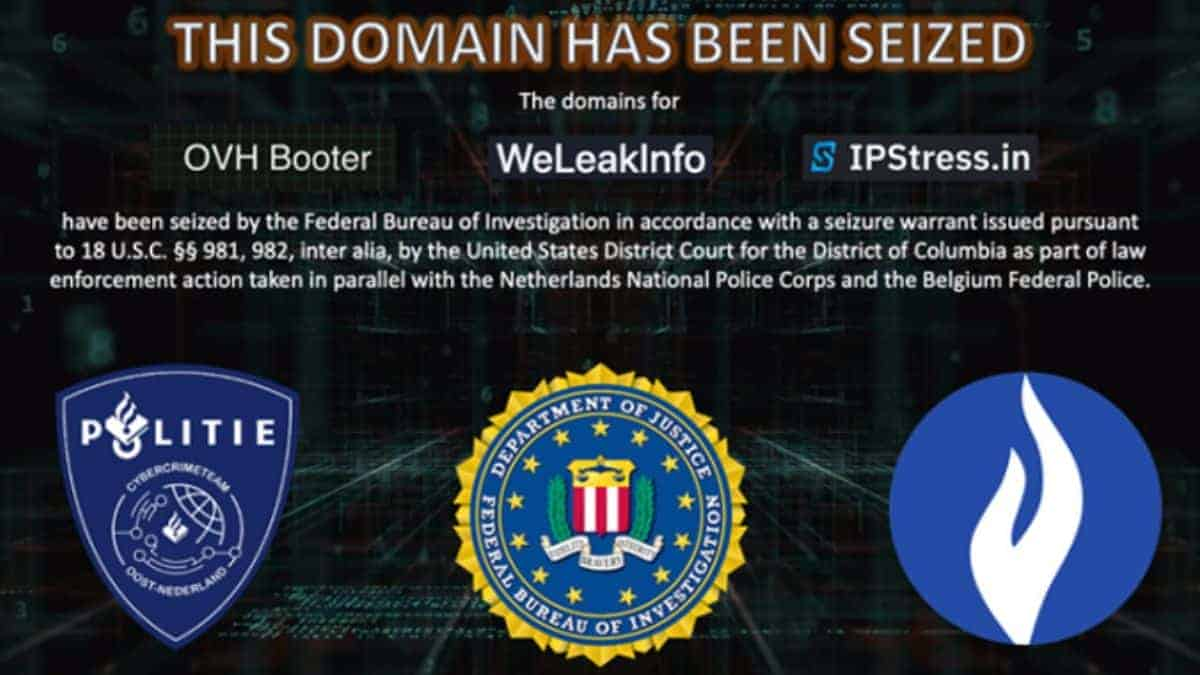
Coming to the seized this is what we know. As per the announcement, the seized domains are: weleakinfo[.]to, ipstress[.]in, and ovh-booter[.]com The first was a cybercrime marketplace that allowed users to sell and trade hijacked personal information. It included a searchable database of data stolen in more than 10,000 data breaches. The website’s database had 7 billion records of personally identifiable information (PII), such as complete names, usernames, phone numbers, email addresses, and login credentials for online accounts (usernames and passwords). These stolen records might be accessed through various subscription tiers.

Authorities seized a domain with a nearly identical name (weleakinfo[.]com) in January 2020 and made 21 arrests in connection with the illegal enterprise. One of the operators of the associated domain was sentenced to two years in prison last year. We also came to know that the other two domains on the listing didn’t sell stolen data, but they did act as cybercrime hotspots. DDoS-as-a-service operations were hosted by Ipstress[.]in and ovh-booter[.]com, where clients may pay a fee to have DDoS assaults on their selected targets using a proxy.
Furthermore, DDoS assaults are cyberattacks that overload machines, resources, or networks with excessive traffic in order to render them inaccessible. When a DDoS assault is successful, the targeted device is unable to handle genuine requests and frequently falls offline until the attack is stopped. The DDoS-related domains delivered booter, or IP stresser, attacks to their customers, as their names suggest.


