New RedAlert Ransomware objects Windows, Linux, VMware ESXi servers

A new ransomware operation which is called RedAlert encrypts both Windows and Linux VMWare ESXi servers in an attack on computer networks. This new operation was found at present by MalwareHunterTeam, who have earlier tweeted of end number of pictures of the group’s information leak website.
The ransomware has been known as ‘RedAlert’ primarily because of a string used within the ransom word. However, from a Linux encryptor acquired by BleepingComputer, they name their operation ‘N13V’ which is shown below.
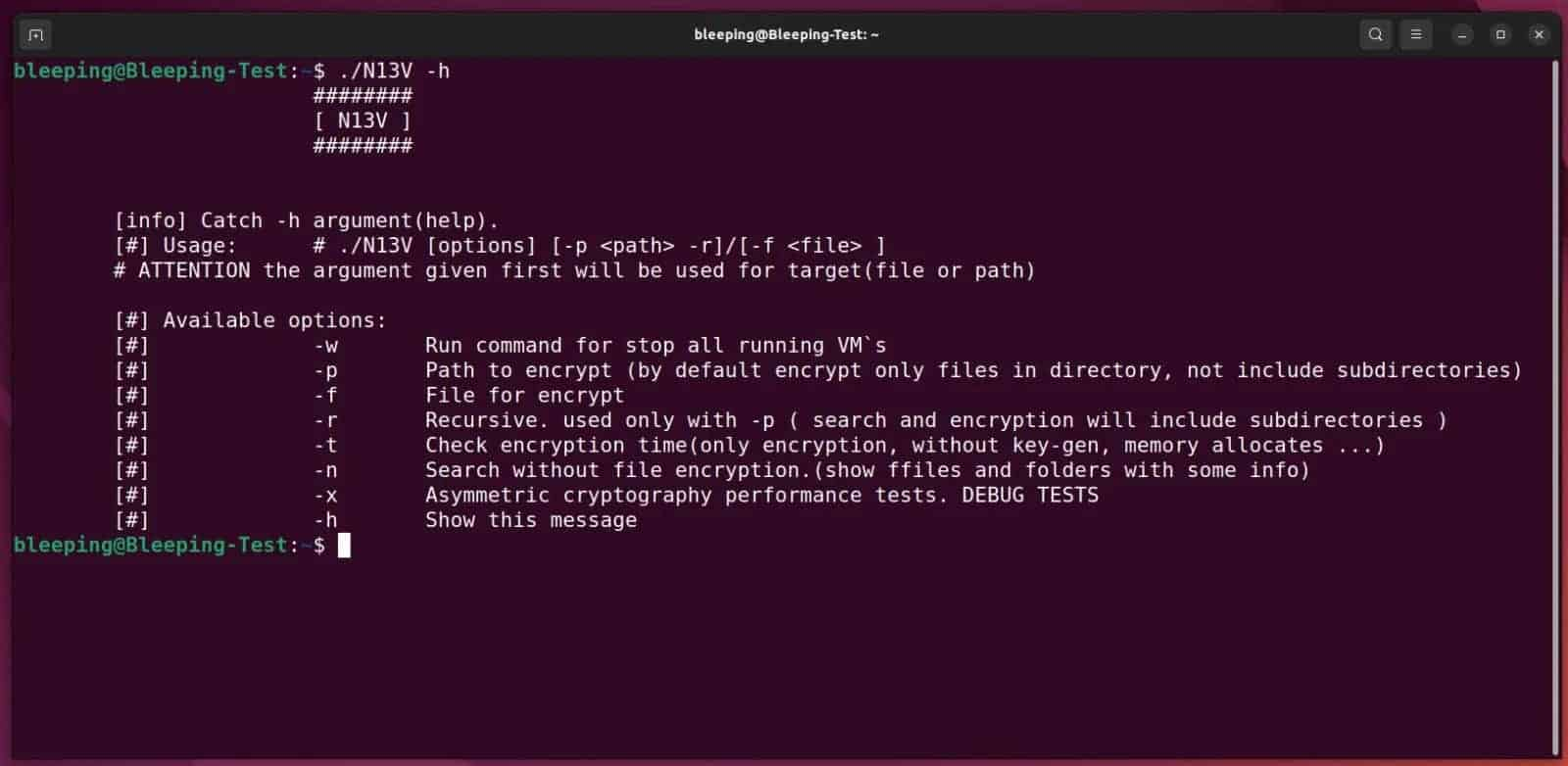
The Linux encryptor is created mainly to focus on VMware ESXI servers, also it has command-line choices that allow the threatened people to close down any working digital machines earlier than authenticating recordsdata. When encrypting records data, the ransomware applies the NTRUEncrypt public-key encryption algorithm, which will help in many ‘Parameter Units’ that supply a completely different line of safety.
One of the very interesting and fascinating features of RedAlert/N13V is the ‘-x’ command line that performs ‘uneven cryptography efficiency testing’ utilizing these totally different NTRUEncrpt parameter units. But it is still unclear if there is any method that will drive a specific parameter set when encrypting and/or if the ransomware will choose an extra environment-friendly one. When encrypting recordsdata, the task of ransomware will be to mainly focus recordsdata that are related to VMware ESXi, digital machines, digital disks and so on.


