SCADA Hacking: What is SCADA | The Default Passwords of SCADA/ICS System

As per the recent tweets, we came to know that many SCADA systems still use the manufacturer’s default passwords for authentication. SCADA security administrators have always relied on “security by obscurity,” but with Shodan and these passwords, they’ll soon be searching for a new job. SCADA Hacker was created with the goal of sharing relevant, frank, and mission-critical information about industrial security of Supervisory Control and Data Acquisition (SCADA), Distributed Control (DCS), and other Industrial Control Systems (ICS) in relation to public media channels.
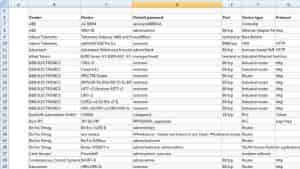
As per the sources, it claims that SCADA Hacker has garnered and sustained over 10,000 readers and followers from over 50 countries since its start in December 2011, making it one of the most important platforms for sharing information and knowledge growth exclusively committed to industrial security. The concept is simple: provide a single point of contact for everything connected to industrial security to a wide variety of readers across numerous industry segments.
Furthermore, fundamental education and knowledge of real-world risks and security flaws that occur within the factory control and automation system architectures used in most process factories and production amenities is an essential part of cyber security for crucial infrastructure safeguard.

Coming to the SCADA attacks previously occurred, this is what we came to know. Stuxnet was one of the most complicated malware known in 2010. It infected control system networks, and others speculated that it may have damaged up to one-fifth of Iran’s nuclear power centrifuges. Because it was the first known threat to target precisely SCADA systems to manipulate networks, the Stuxnet malware served as a wake-up call to SCADA systems worldwide. Another is the Night Dragon, which is a set of Tactics, Techniques, and Procedures (TTPs) that were utilized in a series of coordinated, secret, and targeted cyber-attacks that were made public in 2010.
Moreover, these attacks targeted companies in the oil, energy, and petrochemical industries around the world. Files of interest included financial papers connected to field exploration and bidding, as well as operational oil and gas field production systems. Hackers copied and downloaded files from firm web servers in some circumstances. Hackers also took data from SCADA systems in some circumstances.


