American Express has patched its Open Redirect Flaw while snapchat still hasn’t patched it

Researchers have discovered that attackers are leveraging the American Express and Snapchat domains to phish people’s passwords and personally identifiable information (PII) by taking advantage of a well-known open redirect issue.
Researchers from INKY said in an online blog post that they noticed two distinct campaigns between mid-May and late July in which threat actors impersonated FedEx, Microsoft, and other firms. Attackers used redirect flaws that affected the American Express and Snapchat domains; the former was later patched, but the latter is still not, according to researchers.
Open redirect is a security flaw that appears when a website doesn’t authenticate user input. As a result, bad actors can change the URLs of domains belonging to trustworthy organisations to route people to malicious websites, according to researchers. The vulnerability, known as CWE-601: URL Redirection to Untrusted Site (‘Open Redirect’), is well recognised and tracked.
In the post, INKY’s Roger Kay wrote, “Since the initial domain name in the altered connection is actually the original site’s, the link may appear safe to the casual observer.”
An example of a malicious redirect domain is: http[://]safe[.]com/redirect?[url=http:]//malicious[.]com. The trusted domain, then—in this case, American Express or Snapchat—is used as a temporary landing page before the victim of the campaign is redirected to a malicious site.
Snapchat
INKY engineers found the snapchat[.]com open redirect vulnerability in 6,812 phishing emails sent from multiple accounts that had been compromised over a two-and-a-half-month period.
Here is the link to the phising site of snapchat : https://click.snapchat[.]com/aVHG?=http://29781.google.com&af_web_dp=http://qx.oyhob.acrssd[.]org. #.aHR0cHME6Ly9zdG9yYWdlYXBpLmZsZWVrLmNvLzI0MjY4ZTMyLT E2MEmQtNDUxYi1hNTc4LWZhNzg0OTdiZjM4NC1idWWNrZXQvb2Z maWNlMzY1Lmh0bWwjYWNvb3BlckBjcHRsaGVhbHRoLmNvbQ==
Open Bug Bounty reported the Snapchat vulnerability to the company on Aug. 4, 2021. However, it remains unpatched.
America Express
INKY engineers found the americanexpress[.]com open redirect vulnerability in 2,029 phishing emails that came from recently registered domains over the course of just two days in late July.
Here is the previous link that was used for phishing : https://www.americanexpress[.]com/Tracking?mid=ALE220718AEMLCATENUS120620PM3736&msrc=ALERTS-NOTIF-PLAT&url=http://58a.upwebseo[.]com/ms/aXJAbXdzbM2xhcmVVuZXJneS5jb20=
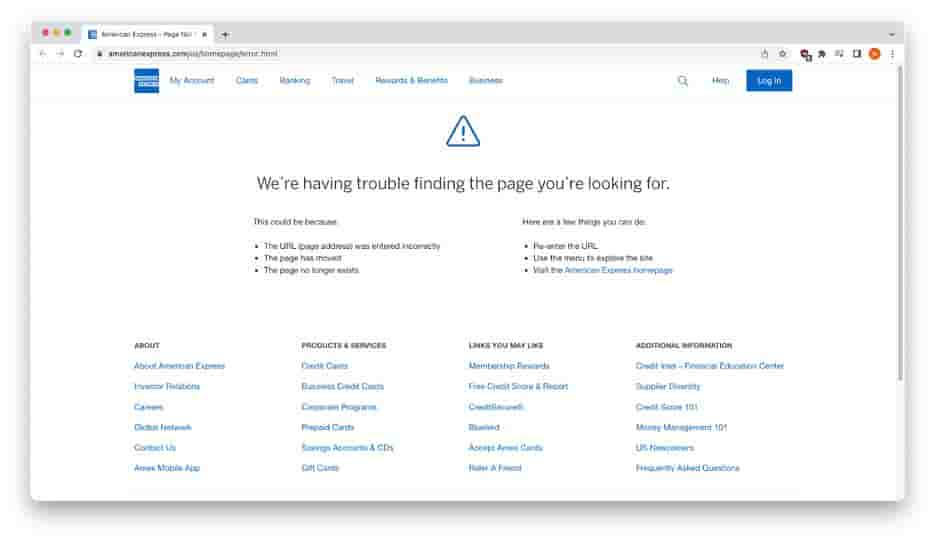
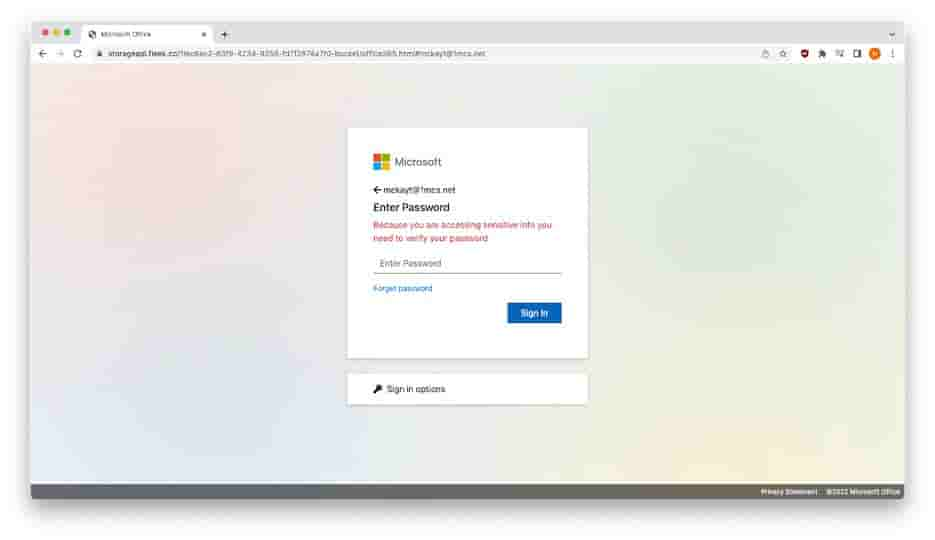
The American Express open redirect link originally led to Microsoft credential harvesting sites when this phishing campaign first began, however, American Express quickly rectified the issue. The URL now directs viewers to a genuine American Express error page.


