Conti Leaks threatens those attacking Russia, with Ransomware attacks

Conti, a ransomware gang that has only been active for two years, has quickly established itself as one of the most successful online extortion groups in history. According to the latest Crypto Crime Report produced by virtual currency tracking firm Chainalysis, it generated a staggering $180 million in income last year alone.
The group virtually exclusively targets businesses with yearly revenues of more than $100 million, allowing it to obtain multimillion-dollar ransom payments from its victims on a regular basis.
The group appeared to be on track to continue in that direction until late last month when it made a critical error by publicly endorsing Russia’s invasion of Ukraine. Someone was plainly offended by the group’s allegiance. The gang’s internal Jabber/XMPP server, which held their private communications channel, was hacked within days, and two years of the group’s chat logs surfaced on a new Twitter handle named @ContiLeaks.
“Greetings,” one tweet began. “Here is a friendly heads-up that the Conti gang has lost its s****” The message included a link that would allow anyone to download almost two years of private chats. “We promise it is very interesting,” the tweet added.
‘Big game hunting’
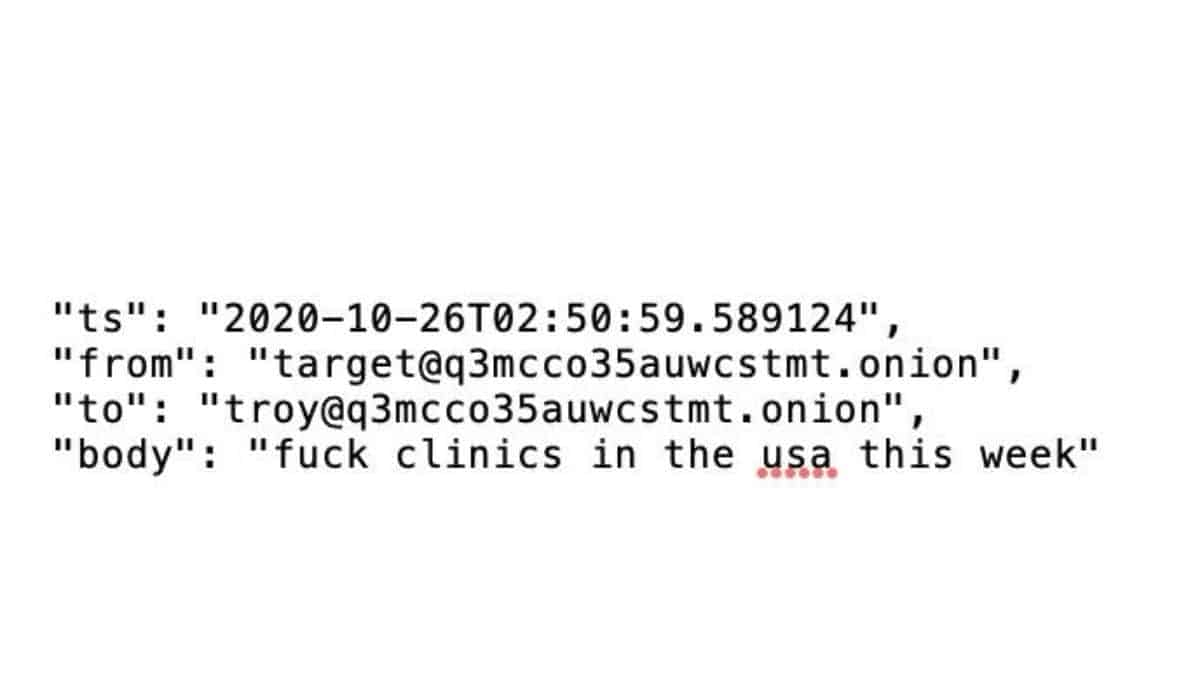
Two Conti hackers established a messaging thread in the fall of 2020. They had their fingertips on keyboards, and they were about to unleash a wave of ransomware attacks on over 400 hospitals in the United States and the United Kingdom. The COVID-19 pandemic was in full stride at the time, and shutting down hospital computers was extremely brutal. “F— the clinics in the United States this week,” said one of the hackers, using the handle ‘Target,’ adding that the attack will undoubtedly cause panic.
Conti specializes in ‘big game hunting,’ which entails digging into the networks of high-value targets – such as large hospital systems – to find vulnerabilities, extracting important information, and then installing malware on their systems to prevent anyone from accessing their data until a ransom is paid.
The gang even used an incentive scheme to get their victims’ attention and focus on what was at stake. Conti hackers would extract vital, sometimes sensitive information before installing the virus, and then explain how much data they obtained and what it would do to the organization if the information was sold or made public in their ransomware note.
“Hi, There! This is the Conti Team,” read one of their ransomware messages captured in a report on the group from Prodaft, a cybersecurity company in Switzerland. “As you already know we have infiltrated your networks… we have downloaded your critical information with a total volume of 450 GB.”
The report then goes on to explain what would happen to the corporation if the information was made public. Then they provided a useful link to a victim-blaming blog that they had created specifically for that purpose. Conti (and its predecessor organisation Ryuk) targeted large corporations such as Garmin, Pitney Bowes, and Tribune Publishing in addition to hospital systems.
‘Like us,’ they say.
Émilio Gonzalez is a security analyst at a financial services company in Canada, where he works on a blue team. That means he protects the company’s computer network from intruders such as Conti. He came across the Twitter chat logs by accident.
“And I thought it was really cool and I wanted to get my eye and my hands on it,” he said from his home office, swinging back and forth in one of those big ergonomic chairs that gamers have. His fingernails are painted black. He’s been reading the chat logs for three days so far. “I have a day job, so I only do it during lunch and the evenings, but I’ve spent a lot of hours on that and I’m not even close to done having seen everything.”
The extent to which he identifies with the Conti hackers whose messages he is reading has startled him. He says, “They’re just like us.” They request paid time off, gossip about coworkers, and make plans with coworkers. “It makes sense to me.” For them, it’s the same. Even if they’re what we consider evil characters, they want to interact with people and enjoy their lives.”
Consider the situation of Target, a Conti manager. He turns out to be a rude employer, the type who expresses his impatience by sending one-word letters like where… are… you? He issued an all-call the Saturday before the hospital attacks, and it wasn’t a request for assistance; it was a demand. He declared, “Everyone is working today.” There was no explanation or apologies.
There is a definite hierarchy in the chats. You’ve got middle management like “Target,” worker bee programmers who develop the harmful code that makes ransomware work, and an IT team that keeps their servers up to date backs up their data, and can quickly break it all down.
Which begs the question of how such a proficient hacking squad could fail to encrypt their discussions.
Conti’s lack of operational security is astounding, according to Discordian, a sort of spokesperson for the hacktivist movement Anonymous.
“The stupid aspect is that they did it in an unencrypted manner,” he stated. “Isn’t that unthinkable?” They must be trembling in their boots right now, because a lot of their identities, as well as a lot of their operations, will be revealed as a result of these disclosures.
This was made possible because of inputs from therecord.media.


