Data Can Be Exfiltrated From Air-Gapped Systems Using Ethernet LEDs
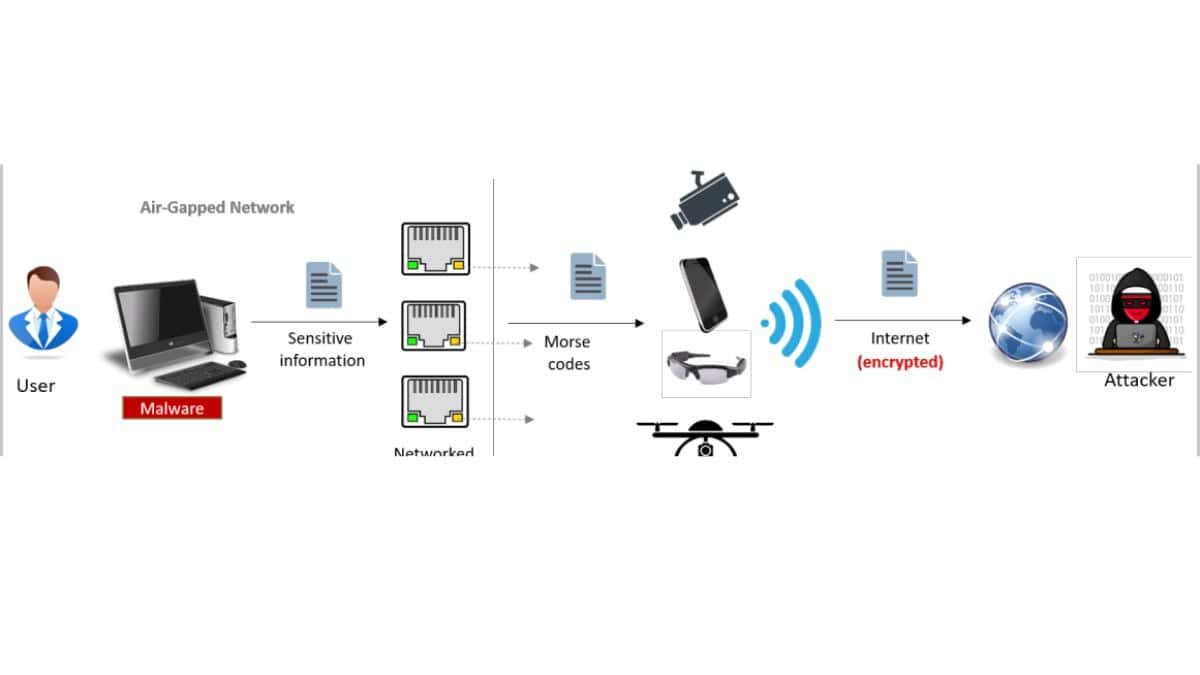
A researcher from the Israel’s Ben-Gurion University of the Negev published a paper describing a way for silently exfiltrating data from air-gapped systems using LEDs from various types of networked devices.
The novel ETHERLED assault is based on LEDs connected to the integrated network interface controller (NIC) of devices such as PCs, servers, printers, network cameras, and embedded controllers.
An attack scenario presupposes that the attacker gained access to the targeted air-gapped device — either through social engineering, hostile insiders, or a supply chain attack — in order to plant malware that collects sensitive data and exfiltrates it to the attacker via a covert route.
Mordechai Guri demonstrated how an attacker may send sensitive information such as passwords, encryption keys, and even text files by encoding and modulating them over optical signals based on the blinking patterns or blinking frequency of Ethernet LEDs.
The NIC normally has two LEDs: an activity LED, which is usually green, and a status LED, which alternates between green and amber depending on the link speed. The status LED, for example, can be amber for 1 Gb connections, green for 100 Mb connections, and off for 10 Mb connections.
The speed with which data can be exfiltrated is determined by the type of modulation utilized and the technology used to regulate the LEDs. Only 1 bit/sec can be exfiltrated when the connection status control technique is used with OOK and blink frequency modulation, but the maximum bit rate increases to 100 bits/sec when the driver/firmware control method is used.
A password can be exfiltrated in one second and a Bitcoin private key in 2.5 seconds when driver/firmware control is used with two LED colors. In less than two minutes, a 1 Kb text file can be taken.


