Devices with Cobalt Strike are infected by new phishing attack
Security researchers have discovered a new malicious spam campaign that uses the ‘Matanbuchus’ virus to infect computers with Cobalt Strike beacons.
Threat actors routinely employ Cobalt Strike, a penetration testing package, for lateral movement and to dump additional payloads.
Matanbuchus is a malware-as-a-service (MaaS) initiative that originally surfaced on the dark web in February 2021 as a $2,500 loader that launches executables straight into system memory.
In June 2021, Palo Alto Networks’ Unit 42 studied it and mapped large portions of its operating architecture. The malware’s characteristics include the ability to run custom PowerShell commands, the use of standalone executables to load DLL payloads, and the use of task schedules to ensure persistence.
Brad Duncan, a threat analyst, obtained a sample of the malware and evaluated it in a lab setting.
The current malspam campaign employs lures that look like replies to prior email conversations, complete with a ‘Re:’ in the subject line.
A ZIP attachment is included in the emails, which contains an HTML page that creates a new ZIP archive. This produces an MSI package that has been digitally signed with a valid DigiCert certificate for “Westeast Tech Consulting, Corp.”
Running the MSI installer is designed to start an Adobe Acrobat font catalogue update, which finishes with an error message, to keep the victim distracted from what’s going on behind the scenes.
Two Matanbuchus DLL payloads (“main.dll”) are dropped in two distinct locations in the background, a scheduled task to preserve persistence through system reboots is formed, and communication with the command and control (C2) server is established.
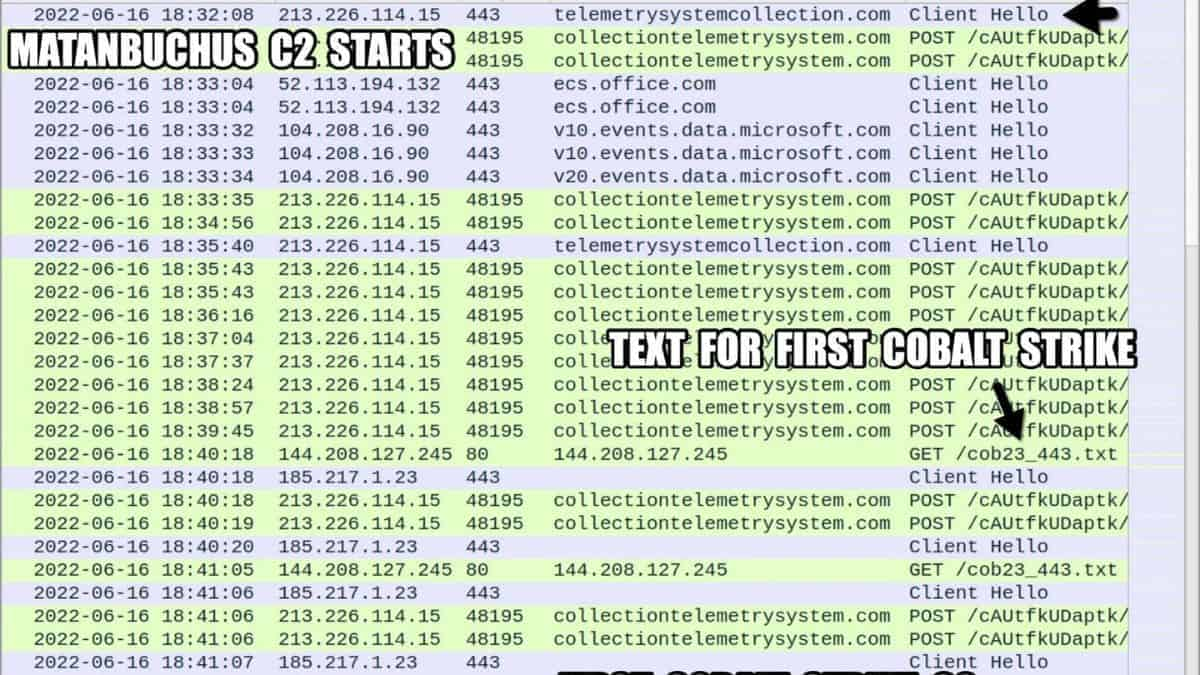
On May 23, 2022, DCSO, a German security firm, first reported Cobalt Strike as a second-stage payload in the Metanbuchus malspam campaign. They also discovered that in certain situations, Qakbot was also provided.
Surprisingly, the digital signature utilised for the MSI file in that campaign was a real DigiCert one provided to “Advanced Access Services LTD.”
Defenders can look at the DCSO data and the IoCs posted by ‘Execute Malware’ on the ongoing campaign for recent indicators of compromise.
Duncan has also made traffic samples, artefacts, examples, and evidence of compromise available on his website (IoCs).


