LAPSUS$ Hackers Allege Breach of Microsoft and Authentication Firm Okta
Microsoft and Okta, a provider of authentication services, said they are looking into claims of a potential breach made by the LAPSUS$ extortionist organisation.
The news was initially reported by Vice and Reuters, who said the cybercriminal gang uploaded screenshots and source code of the companies’ internal projects and systems on its Telegram channel.
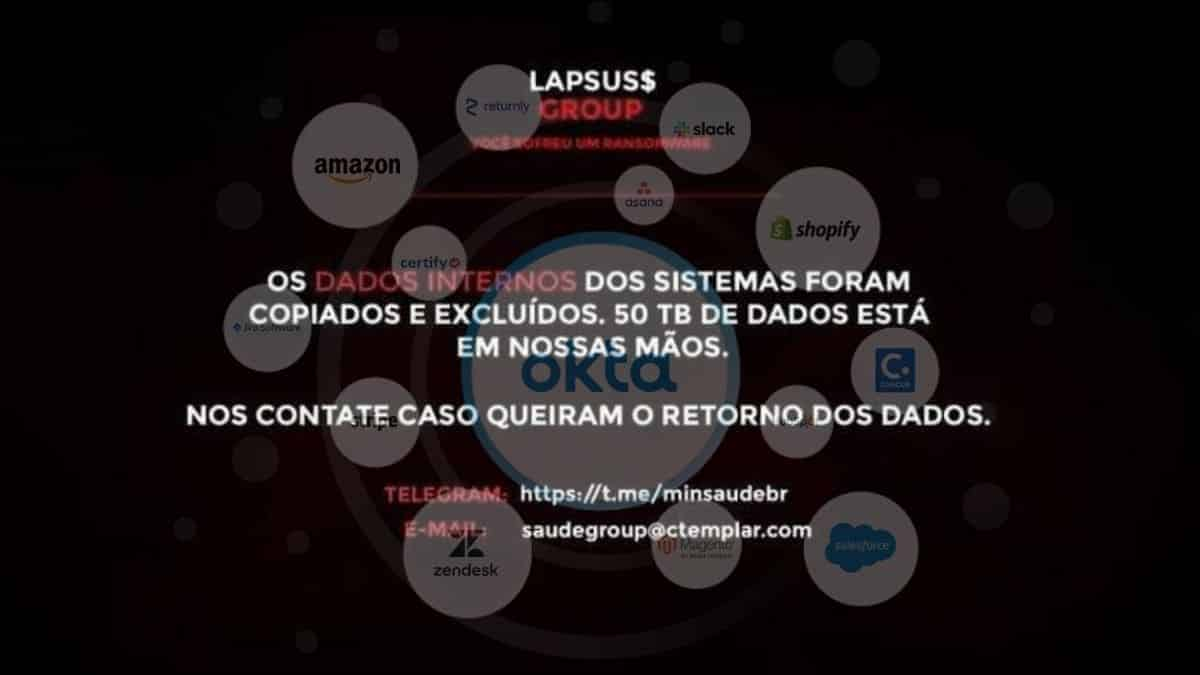
LAPSUS$ extortion group claims to have breached @Okta. They have released 8 photos as proof.
The photos we are sharing has been edited so no sensitive information or user identities are displayed.
Image 1 – 4 attached below. pic.twitter.com/nR8V56dLu2
— vx-underground (@vxunderground) March 22, 2022
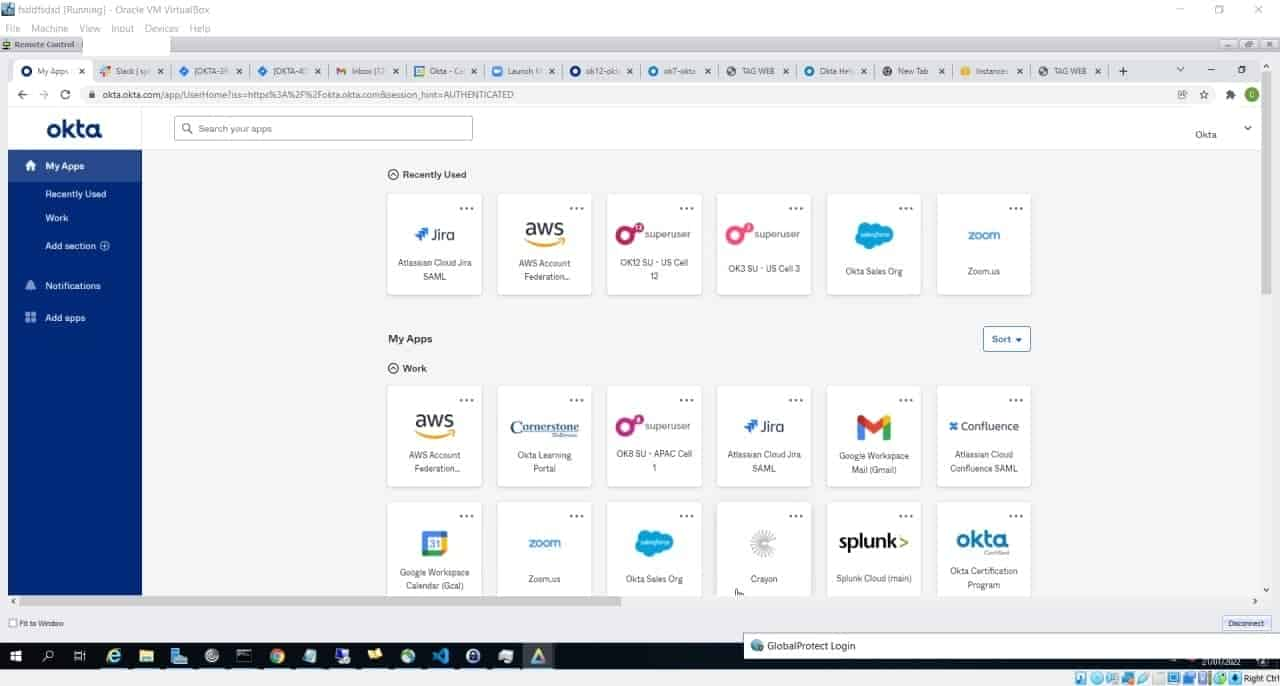
The leaked 37GB folder indicates that the group may have accessed Microsoft’s Bing, Bing Maps, and Cortana repositories, with photographs showing Okta’s Atlassian suite and internal Slack channels.
“For a service that powers authentication systems to many of the largest corporations (and FEDRAMP approved) I think these security measures are pretty poor,” the hacking cartel wrote on Telegram.
On top of this, the group alleged that it breached LG Electronics (LGE) for the “second time” in a year.
Since then, LAPSUS$ has emphasised that it did not penetrate Okta’s databases and that “our focus was ONLY on Okta customers.” This could have major consequences for other government organisations and businesses that utilise Okta to authenticate user access to internal systems.
“In late January 2022, Okta detected an attempt to compromise the account of a third-party customer support engineer working for one of our subprocessors. The matter was investigated and contained by the subprocessor,” Okta CEO Todd McKinnon said in a tweet.
In late January 2022, Okta detected an attempt to compromise the account of a third party customer support engineer working for one of our subprocessors. The matter was investigated and contained by the subprocessor. (1 of 2)
— Todd McKinnon (@toddmckinnon) March 22, 2022
“We believe the screenshots shared online are connected to this January event. Based on our investigation to date, there is no evidence of ongoing malicious activity beyond the activity detected in January,” McKinnon added.


