LockBit 3.0 has a new target The Singapore subsidiary of “Meiji”

LockBit 3.0 (also known as LockBit Black) is a variant of the LockBit ransomware family. This is a group of ransomware programs that were discovered in September 2019, following the first wave of attacks. LockBit was initially referred to as the “.abcd virus,” but it was not known at the time that LockBit’s creators and users would continue to create new iterations of the original ransomware program.
LockBit’s ransomware family is self-replicating, but only certain victims are targeted—primarily those with the means to pay a large ransom. Those who use LockBit ransomware frequently purchase Remote Desktop Protocol (RDP) access on the dark web in order to remotely and easily access victims’ devices.
Since its inception, LockBit’s operators have targeted organizations all over the world, including the United Kingdom, the United States, Ukraine, and France. This malware family employs the Ransomware-as-a-Service (RaaS) model, in which users pay the operators to gain access to a specific type of ransomware. This frequently involves some kind of subscription. Users can sometimes check statistics to see if their LockBit ransomware use was successful.
Recently, Meiji Seika Singapore is hacked by Lock bit 3.0 Ransomware. Meiji Seika Singapore, founded in 1974, is Meiji Co., Ltd. Japan’s first overseas operation, and it is now one of Singapore’s leading food manufacturers.
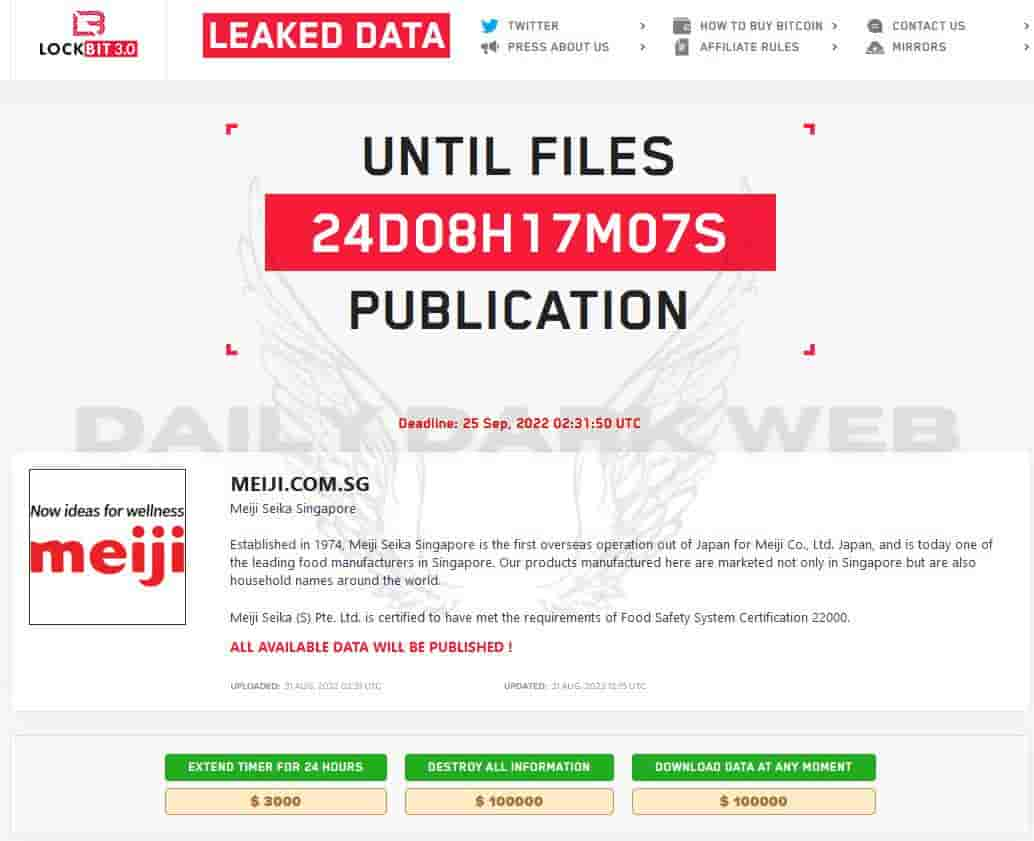
According to the company, it is still investigating the extent of the damage. According to Meiji, it was confirmed on August 29 that its subsidiary in Singapore, Meiji Seika Singapore, which manufactures and sells confectionery, had been infected with a ransomware computer virus. According to the company, it is reporting to Singapore government authorities and investigating the detailed damage situation while continuing business operations such as product manufacturing and sales.
LockBit has updated the timeline for the release of the data to 24 days.


