Microsoft just averted a Russian Espionage APT attack

Microsoft stated on Monday that it had severed access to accounts used for pre-attack reconnaissance, phishing, and email harvesting from an APT actor thought to be affiliated with the Russian government.
Since at least 2017, there has been evidence of the threat actor, known by Microsoft as SEABORGIUM, performing active cyberespionage assaults targeting military personnel, government officials, think tanks, and journalists in Europe and the South Caucasus.
Microsoft’s abuse teams and Redmond’s security research and threat hunting teams collaborated to block phishing domains and disable OneDrive and other accounts connected to Microsoft services.
In addition to revealing the Russian threat actor’s malware infrastructure, Microsoft also disclosed IoCs (indicators of compromise) to assist defenders in looking for infections.
Microsoft cautioned that the APT group’s goals and victimology strongly coincide with Russian state interests based on IOCs and actor methods, and validated SEABORGIUM overlaps with previously published documentation from Google (codename COLDRIVER) and F-Secure (codename Callisto Group).
Microsoft claimed that the organisation engaged in repeated phishing, credential theft, and data theft efforts while abusing the OneDrive service and false LinkedIn profiles.
In addition to doing reconnaissance on LinkedIn, Microsoft discovered the threat actor creating email accounts with consumer email providers with the express intent of using the accounts to appear as real people for more phishing lures.
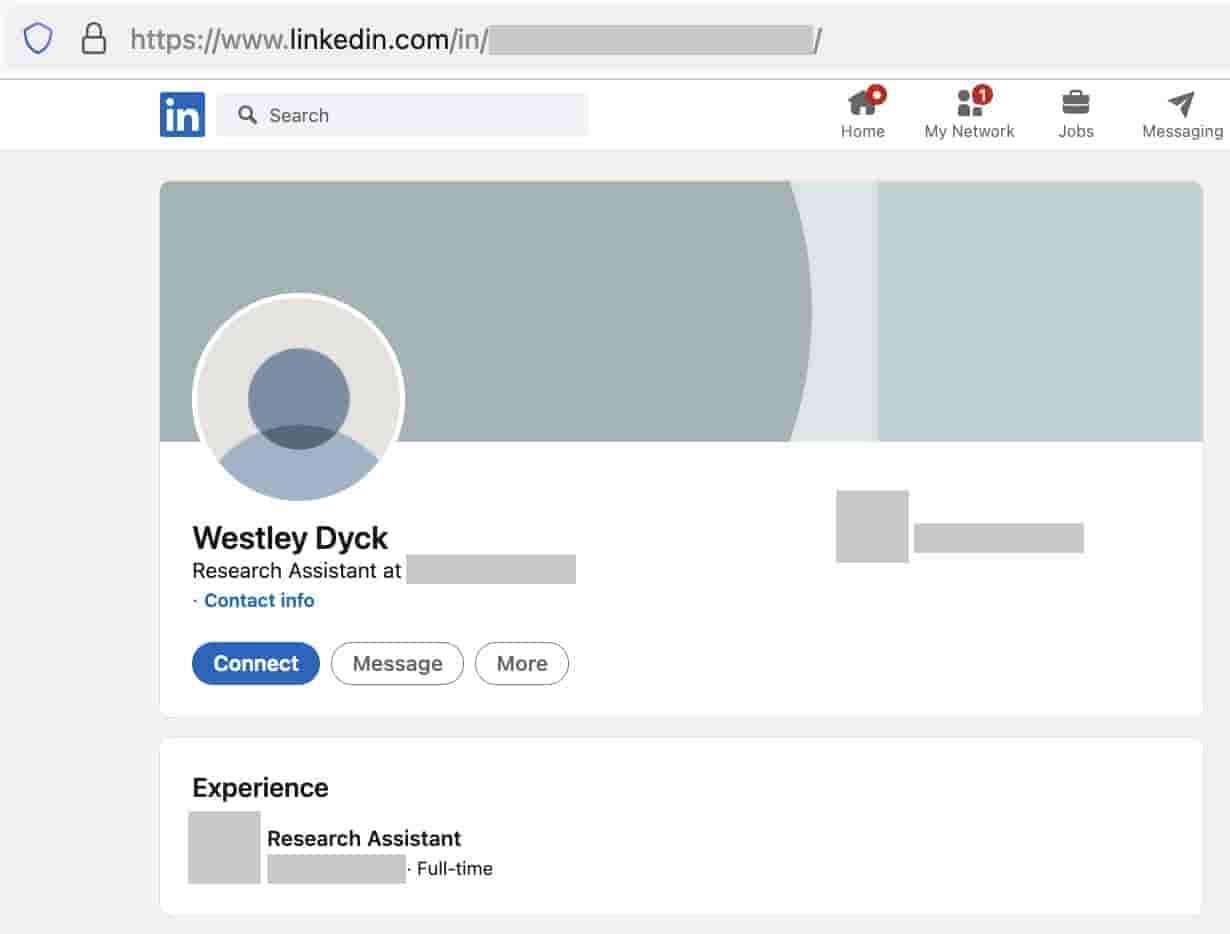
SEABORGIUM frequently undertakes reconnaissance of target individuals prior to launching a campaign, with a focus on finding reliable contacts in the targets’ distant social network or sphere of influence. We believe that the threat actor leverages social networking platforms, personal directories, and general open-source information (OSINT) to support their reconnaissance efforts based on some of the impersonation and targeting that we have witnessed. In collaboration with LinkedIn, MSTIC has noticed that phoney profiles purporting to be from SEABORGIUM are occasionally being used to spy on personnel from particular organisations of interest. LinkedIn cancelled any accounts (including the one displayed below) that were found to be engaging in fraudulent or inauthentic activity in accordance with their policy.
Additionally, SEABORGIUM creates new email accounts at different consumer email providers with email addresses or aliases that are set up to resemble real aliases or names of impersonators. We have seen SEABORGIUM return to and reuse prior accounts that fit the industry of the eventual target, even if the establishment of new consumer accounts is typical. In one instance, we noticed SEABORGIUM accessing an account it hadn’t used in a year, suggesting that accounts might be tracked and reused if they are pertinent to targets’ verticals.


