The operators of the REvil ransomware say that the organisation has ceased operations once more, and that the victim leak blog has been taken offline
Researchers are dubious of this new shut down because the group returned a few weeks ago after stopping shop in July.
According to cybercriminals claiming to be members of the REvil ransomware organisation, the gang is shutting down after losing control of critical infrastructure and experiencing internal strife.
Recorded Dmitry Smilyanets, a future security specialist, published many messages on Twitter from ‘0 neday,’ a notorious REvil operator, describing what transpired on the cybercriminal site XSS. He stated that the group’s Tor payment gateway and data leak website had been hacked.
0 neday says in the mails that he and “Unknown,” a senior member of the gang, were the only two members of the gang who possessed REvil’s domain keys. “Unknown” vanished in July, leading the rest of the gang to believe he had perished. The organisation restarted activities in September, however 0 neday reported this weekend that the REvil domain had been accessed with “Unknown” keys.
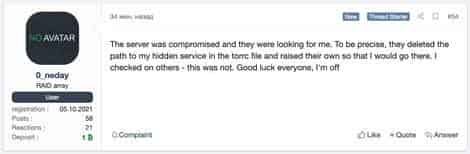
0 neday wrote in another message, “The server had been hacked, and they were on the lookout for me. They removed the route of my secret service from the torrc file and replaced it with their own, causing me to go there. I double-checked with others, and this was not the case. Good luck to everyone; I’m leaving now.”
After the horrific attack on Kaseya spread hundreds of companies worldwide and caused enormous harm, REvil shut down in July. The group is one of the most active ransomware gangs today, having targeted hundreds of important corporations and organisations in recent years.
However, following the July 4 attack on Kaseya, the organisation came under intense law enforcement investigation and terminated its activities on July 13. The gang reappeared in September, continuing to assault scores of businesses in recent weeks.
According to The Record, the group’s servers were shut down on July 13 after “Unknown” reportedly took their money and shut them down, making it impossible for them to reopen.
Smilyanets told the news organisation that he hoped the organisation had been shut down as a result of US law enforcement operations. Because of their activities during the REvil attack on Kaseya, the FBI and other US agencies have experienced substantial blowback in recent weeks.
The FBI confessed it had decryption keys that might have aided the approximately 1,500 ransomware victims afflicted by the Kaseya assault, but opted against it because they were planning an attack on REvil’s infrastructure. The organisation shut down before the operation could be completed, and the FBI has been chastised by the impacted groups and politicians for delaying the release of the decryption keys.
Bitdefender eventually provided a free decryptor to all of the Kaseya-affected enterprises.
Experts had conflicting reactions to the incident, with some advising citizens not to trust criminals’ words. Others explained that the scenario made sense because REvil’s acts were being criticised by its own affiliates.


