Threat Experts found a Snake Keylogger malware distributed using PDF attachments

As per the news floating around the internet, it claims that threat experts found a new malware distribution effort that uses PDF attachments to smuggle dangerous Word documents into users’ computers. Most phishing emails today include DOCX or XLS attachments loaded with malware-loading macro code, thus the use of PDFs is unusual.
Threat actors are switching to different methods to install harmful macros and elude detection as users grow more aware of opening fraudulent Microsoft Office attachments. Researchers show how PDFs are being exploited as a transport for documents containing malicious macros that download and install information-stealing malware on victims’ devices in a new paper from HP Wolf Security.
About the Embedded Word in PDF
According to HP Wolf Security, we came to know that The email content contains ambiguous assurances of reimbursement to the addressee, and the PDF arriving by email is titled “Remittance Invoice.” When the PDF is accessed, Adobe Reader prompts the user to open a DOCX file contained therein, which is unusual and may cause the victim to become confused.
“The file ‘has been verified,” says the Open File prompt below, because the malicious hackers named the embedded document “has been verified.” This message may lead recipients to believe that Adobe has authenticated the file and that it is safe to open.
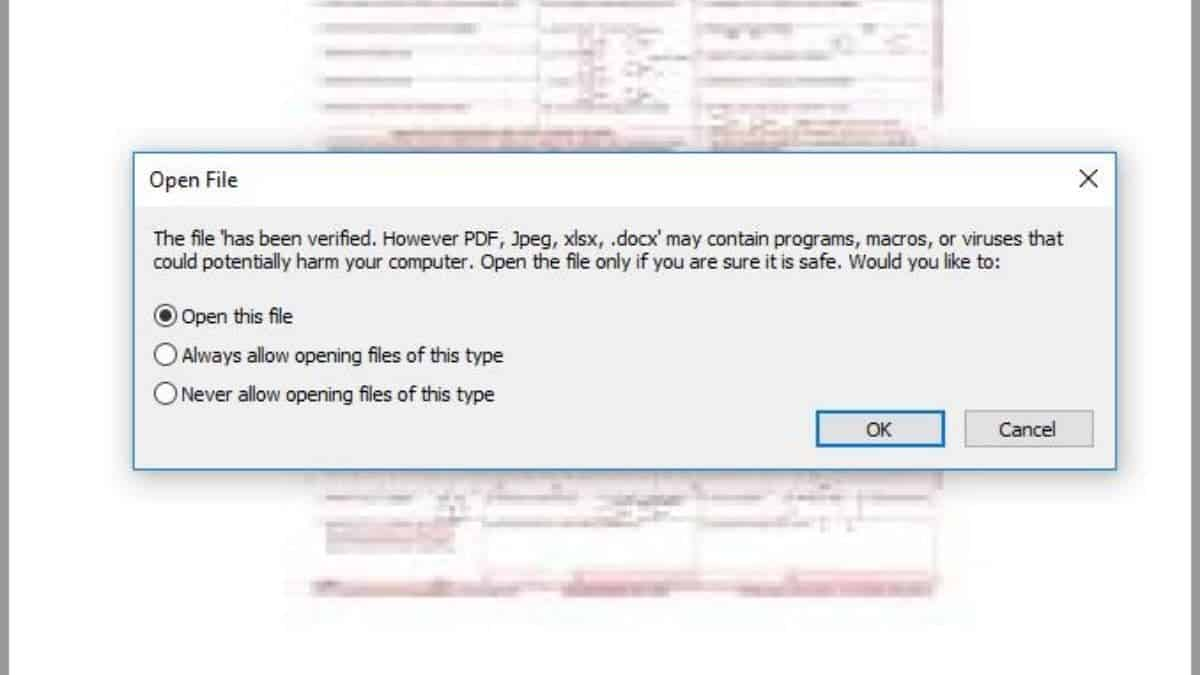
Moreover, while malware investigators can use parsers and scripts to investigate embedded files in PDFs, most average users wouldn’t go that far or even know where to begin. As a result, many people will open the DOCX in Microsoft Word and, if macros are allowed, will download and open an RTF (rich text format) file from a remote location. The following command is inserted in the Word file, coupled with the hardcoded URL “vtaurl.com/IHytw,” which is where the payload is hosted, to download the RTF.
RTF File Contains Malformed OLE
As per the sources, the RTF file is called “f_document shp.doc” and contains faulty OLE objects that are likely to elude detection. HP’s experts discovered that it is attempting to launch arbitrary code by exploiting an outdated Microsoft Equation Editor vulnerability. The shellcode used in the attack targets CVE-2017-11882, a remote code execution flaw in Equation Editor that was addressed in November 2017 but is still exploitable in the wild.
Furthermore, when the vulnerability was revealed, hackers were quick to notice it, and also the lethargic patching became one of the most misused flaws in 2018. The RTF shellcode downloads and runs Snake Keylogger, a modular info-stealer with powerful persistence, defense evasion, credential access, data harvesting, and data exfiltration capabilities, by attacking CVE-2017-11882.


