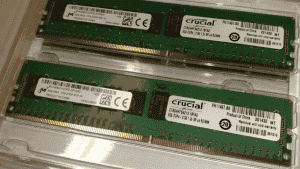
Researchers have found a way to use DDR SDRAM to generate electromagnetic radiation at a 2.4 GHz frequency

To keep confidential knowledge beyond the control of attackers, companies place it on machines that are not wired to a local network, let alone the Internet—so-called air-driven computers. No matter how secure it might sound, infecting such a computer or a network segment is not that difficult. It is much more difficult to retrieve the information gathered.
That’s where all kinds of clever approaches come in, and Mordechai Guri, a scholar at Negev’s Ben-Gurion University, specializes in discovering them. Of course, Dr Guri is not the only one, but he has been interested in the discovery of a few hundred such approaches in recent years.
Recent research explains yet another way to collect data from a remote device, this time using Wi-Fi technology.
How does it work?
The benefit of Air-Fi is that it functions even though the goal machine does not have Wi-Fi facilities. Instead, it relies on malware already mounted on the computer that can use the DDR SDRAM memory bus to produce electromagnetic radiation at a 2.4 GHz frequency. The malware will encrypt the requisite data into variations of this radiation, and any computer with a Wi-Fi receiver, including any other infected device, can pick up and intercept the produced signals. The other gadget may be a standard smartphone or even a smart light bulb.
From a cybersecurity point of view, the Air-Fi approach is extremely nasty. It does not need administrative privileges on an independent computer; a standard user account will get the job done. Furthermore, having a virtual machine does not have protection; VMs provide access to memory modules.
What is the transmission speed and range?
Researchers transmitted data without visible distortions up to 2–3 meters and up to 100 bits per second, depending on the hardware in the contaminated device and the form of a receiver. As for most related approaches, it’s not that easy. For eg, moving a 20MB file will take 466 hours.
What measures you should follow?
The use of Air-Fi includes electromagnetic radiation. You should counter the tactic by taking the following measures:
- Do not allow Wi-Fi devices to close isolated networks for any reason;
- Monitors isolated systems for suspicious processes;
- Shield the computer in the Faraday cage;
- Ban all external electronics, including push-button mobile, in the enterprise.


