What is Sextortion malware scam? and how to protect yourself from it
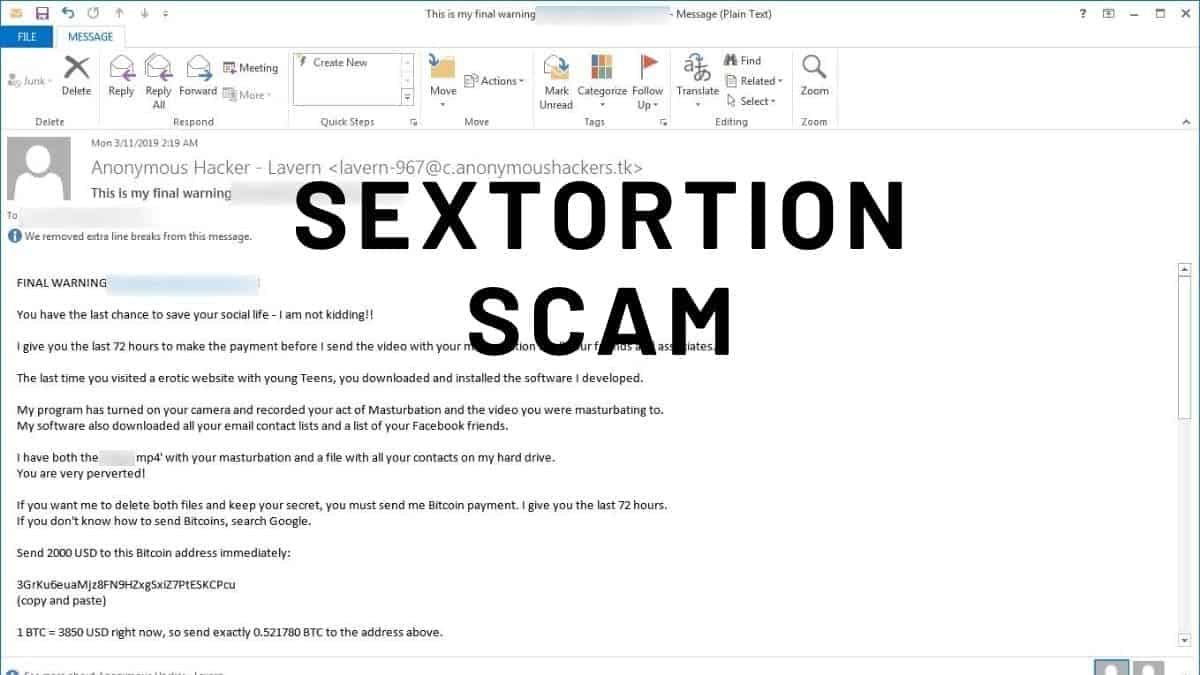
Did you ever receive an email stating “I have full control of your device”. Then you are in the right place and we will explain what is Sextortion Malware scam is in this section.
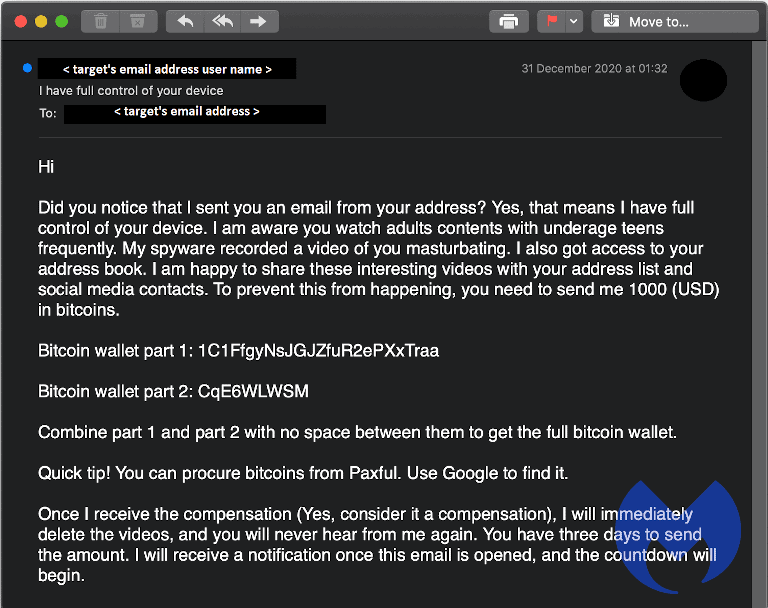
Recently a lot of users have been receiving emails that have content: Move to…
31 December 2020 at 01:32
<target’s email address user name> I have full control of your device To: <target’s email address >
Hi
Did you notice that I sent you an email from your address? Yes, that means I have full control of your device. I am aware you watch adults content with underage teens frequently. My spyware recorded a video of you masturbating. I also got access to your address book. I am happy to share these interesting videos with your address list and social media contacts. To prevent this from happening, you need to send me 1000 (USD) in bitcoins.
Bitcoin wallet part 1: 1C1FtgyNSJGJZfUR2ePXxTraa
Bitcoin wallet part 2: CqE6WLWSM
Combine part 1 and part 2 with no space between them to get the full bitcoin wallet.
Quick tip! You can procure bitcoins from Paxful. Use Google to find it.
Once I receive the compensation (Yes, consider it a compensation), I will immediately delete the videos, and you will never hear from me again. You have three days to send the amount. I will receive a notification once this email is opened, and the countdown will, begin.
What is Sextortion Bitcoin Scam?
Bitcoin sextortion schemes usually send you an email claiming that they’ve videoed you performing sexual actions in private on your webcam and that you must pay them a sum of money in Bitcoin to keep the video (which doesn’t exist) hidden. Since the middle of 2018, this sort of blackmail has grown in popularity.
Sextortion scammers typically contact their victims using faked or made-up email accounts. Those with compromised account passwords scraped from third-party breaches, kids, and other vulnerable categories have been targeted in previous efforts. Our specialists estimate that these emails were almost entirely sent to.org email addresses and senior leadership in this case.
What we may view as a run-of-the-mill, cookie-cutter blackmail email may be novel to someone else, particularly those who are unaware of such a ruse. Make no doubt about it: Email scams that contain little to no threats to recipients have been proven to work time and time again.
This is why it’s critical to stay up to date on what’s going on in the world of cybersecurity, how online risks affect our daily lives, and how we can better protect ourselves, our data, and those around us from those who try to scare, threaten, or bluff their way into our wallets. Treat all emails like this with a healthy dose of suspicion, and you should be able to recognise it for what it is: a hoax.
Throughout the years, Malwarebytes has reported extensively about Bitcoin sextortion frauds. And everything we said back then still holds true for these new sextortion schemes.
Change your passwords, or better yet, use a password manager to help you create and store more complex passwords.
To provide an extra layer of protection, always utilise multi-factor authentication (MFA). This is something that almost every company with a web presence has, so take advantage of it.
Do not hand over any money to the con artist.
Inform your IT department if you receive a sextortion email at work. If you’re in the United States, you can contact the FBI’s IC3 to report this.
Thomas Reed, our Director of Mac and Mobile, had written a blog article addressed to Mac customers who have received similar scammy emails and are unsure what to do.
Stay safe and cautious, as you always should.


